LLDP(Link Local Discovery Protocal)
LLDP是一種標準協議,功能等同思科的CDP,可以探知相鄰設備的設備訊息(版本、介面、平台、功能),思科設備可以用CDP來探知其他思科設備,但若要探知其他廠牌的設備,就需要使用LLDP(思科設備跟他牌設備都需要啟用LLDP)
範例如下:
#在Router1及Router2啟用LLDP:
Router1>enable
Router1#
Router1#configure terminal
Router1(config)#
Router1(config)#lldp run
Router1(config)#end
Router1#
Router2>enable
Router2#
Router2#configure terminal
Router2(config)#
Router2(config)#lldp run
Router2(config)#end
Router2#
#用指令show lldp查看lldp是否已經啟用:
Router1#show lldp
Global LLDP Information:
Status: ACTIVE
LLDP advertisements are sent every 30 seconds
LLDP hold time advertised is 120 seconds
LLDP interface reinitialisation delay is 2 seconds
Router2#show lldp
Global LLDP Information:
Status: ACTIVE
LLDP advertisements are sent every 30 seconds
LLDP hold time advertised is 120 seconds
LLDP interface reinitialisation delay is 2 seconds
#查看LLDP資訊:
Router1#show lldp neighbors
Capability codes:
(R) Router, (B) Bridge, (T) Telephone, (C) DOCSIS Cable Device
(W) WLAN Access Point, (P) Repeater, (S) Station, (O) Other
Device ID Local Intf Hold-time Capability Port ID
Router2 Gig0/0 120 R Gig0/0
Total entries displayed: 1
Router2#show lldp neighbors
Capability codes:
(R) Router, (B) Bridge, (T) Telephone, (C) DOCSIS Cable Device
(W) WLAN Access Point, (P) Repeater, (S) Station, (O) Other
Device ID Local Intf Hold-time Capability Port ID
Router1 Gig0/0 120 R Gig0/0
Total entries displayed: 1
Router1#show lldp neighbors detail
------------------------------------------------
Chassis id: 0005.5E3E.9101
Port id: Gig0/0
Port Description: GigabitEthernet0/0
System Name: Router2
System Description:
Cisco IOS Software, C1900 Software (C1900-UNIVERSALK9-M), Version 15.1(4)M4, RELEASE SOFTWARE (fc2)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2012 by Cisco Systems, Inc.
Compiled Thurs 5-Jan-12 15:41 by pt_team
Time remaining: 90 seconds
System Capabilities: R
Enabled Capabilities: R
Management Addresses - not advertised
Auto Negotiation - supported, enabled
Physical media capabilities:
1000baseT(FD)
1000baseT(HD)
Media Attachment Unit type: 10
Vlan ID: 1
Router2#show lldp neighbors detail
------------------------------------------------
Chassis id: 0005.5E32.5201
Port id: Gig0/0
Port Description: GigabitEthernet0/0
System Name: Router1
System Description:
Cisco IOS Software, C1900 Software (C1900-UNIVERSALK9-M), Version 15.1(4)M4, RELEASE SOFTWARE (fc2)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2012 by Cisco Systems, Inc.
Compiled Thurs 5-Jan-12 15:41 by pt_team
Time remaining: 90 seconds
System Capabilities: R
Enabled Capabilities: R
Management Addresses - not advertised
Auto Negotiation - supported, enabled
Physical media capabilities:
1000baseT(FD)
1000baseT(HD)
Media Attachment Unit type: 10
Vlan ID: 1
Total entries displayed: 1
網路工程師雜記
本網誌僅用於個人學習紀錄,無法確保內容100%正確!
2019年7月25日 星期四
Cisco SDM Template
Cisco SDM Template
思科在Distribution Layer等級的交換器上設計了效能管理樣板(SDM),目的是用於管理與有效分配記憶體資源
指令show sdm prefer會顯示目前設備使用的SDM樣板以及此樣板分配的資源
指令sdm prefer 可切換設備的SDM樣板到指定的類型
範例如下:
Switch>en
Switch#show sdm prefer //檢視設備目前使用的SDM樣板
The current template is "desktop default" template.
The selected template optimizes the resources in
the switch to support this level of features for
8 routed interfaces and 1024 VLANs.
number of unicast mac addresses: 6K
number of IPv4 IGMP groups + multicast routes: 1K
number of IPv4 unicast routes: 8K
number of directly-connected IPv4 hosts: 6K
number of indirect IPv4 routes: 2K
number of IPv4 policy based routing aces: 0
number of IPv4/MAC qos aces: 0.5K
number of IPv4/MAC security aces: 1K
Switch#config terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#
Switch(config)#
Switch(config)#sdm prefer ? //確認可以使用的SDM樣板
access Access bias
default Default bias
dual-ipv4-and-ipv6 Support both IPv4 and IPv6
routing Unicast bias
vlan Vlan bias
Switch(config)#sdm prefer dual-ipv4-and-ipv6 ? //指定資源傾向性
default Default bias \\無傾向性,沒有特別目的的話,選這個就行了
routing Unicast bias \\routing相關功能分配較多資源
vlan Vlan bias \\vlan相關功能分配較多資源
Switch(config)#sdm prefer dual-ipv4-and-ipv6 default
Changes to the running SDM preferences have been stored, but cannot take effect until the next reload.
Use 'show sdm prefer' to see what SDM preference is currently active.
Switch(config)#end
Switch#
%SYS-5-CONFIG_I: Configured from console by console
Switch#wr
Building configuration...
[OK]
Switch#reload
Proceed with reload? [confirm]
----------等設備重開機完成後----------
Switch>en
Switch#show sdm prefer
The current template is "desktop IPv4 and IPv6 default" template.
The selected template optimizes the resources in
the switch to support this level of features for
8 routed interfaces and 1024 VLANs.
number of unicast mac addresses: 2K
number of IPv4 IGMP groups + multicast routes: 1K
number of IPv4 unicast routes: 3K
number of directly-connected IPv4 hosts: 2K
number of indirect IPv4 routes: 1K
number of IPv6 multicast groups: 1.125k
number of directly-connected IPv6 addresses: 2K
number of indirect IPv6 unicast routes: 1K
number of IPv4 policy based routing aces: 0
number of IPv4/MAC qos aces: 0.5K
number of IPv4/MAC security aces: 1K
number of IPv6 policy based routing aces: 0
number of IPv6 qos aces: 0.625k
number of IPv6 security aces: 0.5K
Switch#
切換為dual-ipv4-and-ipv6 routing:
The current template is "desktop IPv4 and IPv6 routing" template.
The selected template optimizes the resources in
the switch to support this level of features for
8 routed interfaces and 1024 VLANs.
number of unicast mac addresses: 1.5K
number of IPv4 IGMP groups + multicast routes: 1K
number of IPv4 unicast routes: 2.75K
number of directly-connected IPv4 hosts: 1.5K
number of indirect IPv4 routes: 1.25K
number of IPv6 multicast groups: 1.125k
number of directly-connected IPv6 addresses: 1.5K
number of indirect IPv6 unicast routes: 1.25K
number of IPv4 policy based routing aces: 0.25K
number of IPv4/MAC qos aces: 0.5K
number of IPv4/MAC security aces: 0.5K
number of IPv6 policy based routing aces: 0.25K
number of IPv6 qos aces: 0.625k
number of IPv6 security aces: 0.5K
切換為dual-ipv4-and-ipv6 vlan:
The current template is "desktop IPv4 and IPv6 vlan" template.
The selected template optimizes the resources in
the switch to support this level of features for
8 routed interfaces and 1024 VLANs.
number of unicast mac addresses: 8K
number of IPv4 IGMP groups + multicast routes: 1K
number of IPv4 unicast routes: 0
number of IPv6 multicast groups: 1.125k
number of directly-connected IPv6 addresses: 0
number of indirect IPv6 unicast routes: 0
number of IPv4 policy based routing aces: 0
number of IPv4/MAC qos aces: 0.5K
number of IPv4/MAC security aces: 1K
number of IPv6 policy based routing aces: 0
number of IPv6 qos aces: 0.625k
number of IPv6 security aces: 0.5K
思科在Distribution Layer等級的交換器上設計了效能管理樣板(SDM),目的是用於管理與有效分配記憶體資源
指令show sdm prefer會顯示目前設備使用的SDM樣板以及此樣板分配的資源
指令sdm prefer 可切換設備的SDM樣板到指定的類型
範例如下:
Switch>en
Switch#show sdm prefer //檢視設備目前使用的SDM樣板
The current template is "desktop default" template.
The selected template optimizes the resources in
the switch to support this level of features for
8 routed interfaces and 1024 VLANs.
number of unicast mac addresses: 6K
number of IPv4 IGMP groups + multicast routes: 1K
number of IPv4 unicast routes: 8K
number of directly-connected IPv4 hosts: 6K
number of indirect IPv4 routes: 2K
number of IPv4 policy based routing aces: 0
number of IPv4/MAC qos aces: 0.5K
number of IPv4/MAC security aces: 1K
Switch#config terminal
Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#
Switch(config)#
Switch(config)#sdm prefer ? //確認可以使用的SDM樣板
access Access bias
default Default bias
dual-ipv4-and-ipv6 Support both IPv4 and IPv6
routing Unicast bias
vlan Vlan bias
Switch(config)#sdm prefer dual-ipv4-and-ipv6 ? //指定資源傾向性
default Default bias \\無傾向性,沒有特別目的的話,選這個就行了
routing Unicast bias \\routing相關功能分配較多資源
vlan Vlan bias \\vlan相關功能分配較多資源
Switch(config)#sdm prefer dual-ipv4-and-ipv6 default
Changes to the running SDM preferences have been stored, but cannot take effect until the next reload.
Use 'show sdm prefer' to see what SDM preference is currently active.
Switch(config)#end
Switch#
%SYS-5-CONFIG_I: Configured from console by console
Switch#wr
Building configuration...
[OK]
Switch#reload
Proceed with reload? [confirm]
----------等設備重開機完成後----------
Switch>en
Switch#show sdm prefer
The current template is "desktop IPv4 and IPv6 default" template.
The selected template optimizes the resources in
the switch to support this level of features for
8 routed interfaces and 1024 VLANs.
number of unicast mac addresses: 2K
number of IPv4 IGMP groups + multicast routes: 1K
number of IPv4 unicast routes: 3K
number of directly-connected IPv4 hosts: 2K
number of indirect IPv4 routes: 1K
number of IPv6 multicast groups: 1.125k
number of directly-connected IPv6 addresses: 2K
number of indirect IPv6 unicast routes: 1K
number of IPv4 policy based routing aces: 0
number of IPv4/MAC qos aces: 0.5K
number of IPv4/MAC security aces: 1K
number of IPv6 policy based routing aces: 0
number of IPv6 qos aces: 0.625k
number of IPv6 security aces: 0.5K
Switch#
切換為dual-ipv4-and-ipv6 routing:
The current template is "desktop IPv4 and IPv6 routing" template.
The selected template optimizes the resources in
the switch to support this level of features for
8 routed interfaces and 1024 VLANs.
number of unicast mac addresses: 1.5K
number of IPv4 IGMP groups + multicast routes: 1K
number of IPv4 unicast routes: 2.75K
number of directly-connected IPv4 hosts: 1.5K
number of indirect IPv4 routes: 1.25K
number of IPv6 multicast groups: 1.125k
number of directly-connected IPv6 addresses: 1.5K
number of indirect IPv6 unicast routes: 1.25K
number of IPv4 policy based routing aces: 0.25K
number of IPv4/MAC qos aces: 0.5K
number of IPv4/MAC security aces: 0.5K
number of IPv6 policy based routing aces: 0.25K
number of IPv6 qos aces: 0.625k
number of IPv6 security aces: 0.5K
切換為dual-ipv4-and-ipv6 vlan:
The current template is "desktop IPv4 and IPv6 vlan" template.
The selected template optimizes the resources in
the switch to support this level of features for
8 routed interfaces and 1024 VLANs.
number of unicast mac addresses: 8K
number of IPv4 IGMP groups + multicast routes: 1K
number of IPv4 unicast routes: 0
number of IPv6 multicast groups: 1.125k
number of directly-connected IPv6 addresses: 0
number of indirect IPv6 unicast routes: 0
number of IPv4 policy based routing aces: 0
number of IPv4/MAC qos aces: 0.5K
number of IPv4/MAC security aces: 1K
number of IPv6 policy based routing aces: 0
number of IPv6 qos aces: 0.625k
number of IPv6 security aces: 0.5K
2018年3月27日 星期二
Redundant Internet connections (5.2.1 and higher) 備援網路連線(針對5.2.1及以上的版本)
Redundant Internet connections (5.2.1 and higher)
In this example, you will create a WAN link interface that provides your FortiGate unit with redundant Internet connections from two Internet service providers (ISPs). The WAN link interface combines these two connections into a single interface.
在此範例中,您將會建置一組虛擬的WAN線路來確保您的FortiGate設備在兩組網際網路的線路上具有備援網路連線的能力。這個WAN虛擬線路將會合併原有的兩組線路為一個單一的介面。
This example includes weighted load balancing so that most of your Internet traffic is handled by one ISP.
此方法僅針對FortiOS版本5.2.1及以上版本。
此範例包含比重負載平衡的設定,所以大多數時候,您的網路流量只會流經其中一條ISP業者提供的網路線路。
A video of this recipe can be found here
此方法的教學影片可在這裡找到(英文影片)
This recipe is only for FortiOS releases 5.2.1 and higher.
此方法僅適用於5.2.1及以上版本
1. Connecting your ISPs to the FortiGate
連接您的ISP設備與FortiGate設備Connect your ISP devices to your FortiGate so that the ISP you wish to use for most traffic is connected to WAN1 and the other connects to WAN2.
將您的ISP設備(小烏龜)與FortiGate設備連接,其中,將您希望使用的流量較大的線路(主線路)連接到WAN1,而另一條線路(備援線路)則連接到WAN2
2. Deleting security policies and routes that use WAN1 or WAN2
將防火牆規則中,有使用到WAN1或WAN2兩條線路的規則全部刪除You will not be able to add an interface to the WAN link interface if it is already used in the FortiGate’s configuration, so you must delete any policies or routes that use either WAN1 or WAN2.
若是在FortiGate上仍有與WAN1或WAN2兩條線路相關的防火牆規則存在,您將無法建立WAN線路介面,所以,您必須將任何會使用到WAN1或WAN2線路的防火牆規則或是路由規則給移除掉。
大多數FortiGate模組在預設時即存在一條使用到WAN1的防火牆規則,這條預設規則也必須刪除才行。
Go to Policy & Objects > Policy > IPv4 and delete any policies that use WAN1 or WAN2.
點選到"政策&物件" > 政策 > IPv4,刪除任何有使用到WAN1或WAN2的政策
Go to Router > Static > Static Routes and delete any routes that use WAN1 or WAN2.
點選到 路由 > 靜態 > 靜態路由,刪除任何有使用到WAN1或WAN2的政策
3. Creating a WAN link interface
建立虛擬WAN線路Go to System > Network > WAN Link Load Balancing.
點選到 系統 > 網路 > WAN端連線平衡負載
Set WAN Load Balancingto Weighted Round Robin. This will allow you to prioritize the WAN1 interface so that more traffic uses it.
在 WAN端連線平衡負載 項目,點選到加權輪循。此操作可以讓您提高WAN1介面被使用的優先順序,如此一來,大多數的流量都會優先通過WAN1。
在"介面群組"中加入WAN1到清單中,將"權重"設為3,並將您的ISP業者提供的Gateway IP設定上去。
You can optionally configure Health Checkto verify that WAN1 can connect to the Internet.
您可以選擇性的設定 "量測線路品質" 以確認WAN1線路可以正常連接到網際網路上
Do the same for WAN2, but instead set Weightto 1.
參照WAN1的設定方式來設定WAN2,但要將"權重"設為1
You can optionally configure Health Checkto verify that WAN2 can connect to the Internet.
您可以選擇型的設定 "量測線路品質" 以確認WAN2線路可以正常連接到網際網路上
The weight settings will cause 75% of traffic to use WAN1, with the remaining 25% using WAN2.
這項比重設定會使大約75%的流量使用WAN 1線路,而其餘的25%流量則會流經WAN 2線路。
4. Creating a default route for the WAN link interface
建立一組路由規則給新建的WAN線路介面使用Go to Router > Static > Static Routes and create a new default route.
點選到 "路由" > "靜態" > "靜態路由",並建立一組新的預設路由。
Device(設備)設為WAN link Interface。
5. Allowing traffic from the internal network to the WAN link interface
允許流量從內部網路流向WAN線路介面Go to Policy & Objects > Policy > IPv4 and create a new policy.
點選到 "政策&物件 > 政策 > IPv4,建立一組新的政策(防火牆規則)
Set Incoming Interfaceto your internal network’s interface and set Outgoing Interfaceto the WAN link interface.
將進入介面設為您的內部網路,將外出介面設為WAN線路介面
Turn on NAT
啟用NAT功能(在政策設定中確認NAT狀態為ON)
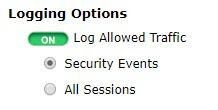
Scroll down to view the Logging Options. To view the results later, turn on Log Allowed Traffic and select All Sessions.
將畫面下拉,檢視到紀錄設定選項,為了稍後可以檢視到紀錄,確認此項目的狀態為ON,並請點選到"全部連線會話"
-----------------------------------以上為實作,以下為結果----------------------------------
6. Results
結果Browse the Internet using a PC on the internal network and then go to System > FortiView > All Sessions
找台電腦,用網頁瀏覽器連到FortiGate的管理網頁,登入並點選到 "系統" > FortiView > "全部連線對話"
Ensure that the Dst Interface column is visible in the traffic log. If it is not shown, right-click on the title row and select Dst Interfacefrom the dropdown menu. Scroll to the bottom of the menu and select Apply.
確保 Dst Interface(目的介面)的攔位在記錄(Log)中可以被找到。若找不到,在標題列上點右鍵(或在右上角的齒輪上點左鍵),選擇Dst Interface(目的介面),點擊Apply(採用)。
The log shows traffic flowing through both WAN1 and WAN2
在紀錄中,Dst Interface(目的介面)應該同時檢視到WAN 1及WAN 2的存在,並能檢視到流經兩者的流量。
Disconnect the WAN1 port, continue to browse the Internet, and refresh the traffic log. All traffic is now flowing through WAN2, until you reconnect WAN1.
中斷WAN 1線路的連線(拔線or關閉Wan 1介面),重整網頁後,繼續檢視網頁上的紀錄,更新流量狀態後(左上角有個重整按紐),再次檢視流量紀錄,此時,所有的紀錄中,所有的流量應應全部流經WAN 2線路,直到您恢復WAN 1線路的連線後,才會恢復到WAN1、WAN2並存的狀態。
Redundant Internet connections(5.2.0) 備援網路連線(只針對5.2.0版本)
Redundant Internet connections (5.2.0)
備援網路連線(只針對5.2.0版本)
在範例中,您將會建置一組虛擬的WAN線路來確保您的FortiGate設備在兩組網際網路的線路上具有備援網路連線的能力。
This example includes weighted load balancing so that most of your Internet traffic is handled by one ISP.
此範例包含比重負載平衡的設定,所以大多數時候,您的網路流量只會流經其中一條ISP業者提供的網路線路。
This recipe is only for FortiOS 5.2.0.
這個方法只適用於FortiOS版本5.2.0
1. Connecting your ISPs to the FortiGate
連接您的ISP設備與FortiGate設備
將您的ISP設備(小烏龜)與FortiGate設備連接,其中,將您希望使用的流量較大的線路(主線路)連接到WAN1,而另一條線路(備援線路)則連接到WAN2
2. Deleting security policies and routes that use WAN1 or WAN2
將防火牆規則中,有使用到WAN1或WAN2兩條線路的規則全部刪除
You will not be able to add an interface to the virtual WAN link if it is already used in the FortiGate’s configuration, so you must delete any policies or routes that use either WAN1 or WAN2.
若是在FortiGate上仍有與WAN1或WAN2兩條線路相關的防火牆規則存在,您將無法建立虛擬的WAN線路,所以,您必須將任何會使用到WAN1或WAN2線路的防火牆規則或是路由規則給移除掉。
Many FortiGate models include a default Internet access policy that uses WAN1. This policy must also be deleted.
大多數FortiGate模組在預設時即存在一條使用到WAN1的防火牆規則,這條預設規則也必須刪除才行。
點選到"政策&物件" > 政策 > IPv4,刪除任何有使用到WAN1或WAN2的政策
Go to Router > Static > Static Routes and delete any routes that use WAN1 or WAN2.
點選到 路由 > 靜態 > 靜態路由,刪除任何有使用到WAN1或WAN2的政策
3. Creating a virtual WAN link
建立虛擬WAN線路
Go to System > Network > Interfaces and select Create New > Virtual WAN.
點選到 系統 > 網路 > 介面,點擊Create New旁邊的下拉選單 > Virtual WAN
Set WAN Load Balancing to Weighted Round Robin. This will allow you to prioritize the WAN1 interface so that more traffic uses it.
在 WAN Load Balancing 項目,點選到加權輪循。此操作可以讓您提高WAN1介面被使用的優先順序,如此一來,大多數的流量都會優先通過WAN1。
Add WAN1 to the list of Interface Members, set Weight to 3, and set it to use the Gateway IP provided by your ISP.
在"介面群組"中加入WAN1到清單中,將"權重"設為3,並將您的ISP業者提供的Gateway IP設定上去。
You can optionally configure Health Check to verify that WAN1 can connect to the Internet
您可以選擇性的設定 "量測線路品質"以確認WAN1線路可以正常連接到網際網路上
Do the same for WAN2, but instead set Weight to 1.
參照WAN1的設定方式來設定WAN2,但要將"權重"設為1
You can optionally configure Health Checkto verify that WAN2 can connect to the Internet.
您可以選擇型的設定 "量測線路品質"以確認WAN2線路可以正常連接到網際網路上
The weight settings will cause 75% of traffic to use WAN1, with the remaining 25% using WAN2.
這項比重設定會使大約75%的流量使用WAN 1線路,而其餘的25%流量則會流經WAN 2線路。
4. Creating a default route for the virtual WAN link
建立一組路由規則給新建的虛擬WAN線路使用
Go to Router > Static > Static Routes and create a new default route.
Set Device to the virtual WAN link.
點選到 "路由" > "靜態" > "靜態路由",並建立一組新的預設路由。
目標IP/遮罩:0.0.0.0/0.0.0.0
設備(介面):virtual WAN link
Distence:10
Priority:0
5. Allowing traffic from the internal network to the virtual WAN link
允許流量從內部網路流向虛擬WAN線路
Go to Policy & Objects > Policy > IPv4 and create a new policy.
Set Incoming Interface to your internal network’s interface and set Outgoing Interface to the virtual WAN link.
點選到 "政策&物件 > 政策 > IPv4,建立一組新的政策(防火牆規則),將進入介面設為您的內部網路,將外出介面設為虛擬WAN線路
Turn on NAT
啟用NAT功能(在政策設定中確認NAT狀態為ON)
Scroll down to view the Logging Options. To view the results later, turn on Log Allowed Traffic and select All Sessions.
將畫面下拉,檢視到紀錄設定選項,為了稍後可以檢視到紀錄,確認此項目的狀態為ON,並請點選到"全部連線會話"
-----------------------------------以上為實作,以下為結果----------------------------------
-----------------------------------以上為實作,以下為結果----------------------------------
6. Results
結果
Browse the Internet using a PC on the internal network and then go to System > FortiView > All Sessions.
找台電腦,用網頁瀏覽器連到FortiGate的管理網頁,登入並點選到 "系統" > FortiView > "全部連線對話"
找台電腦,用網頁瀏覽器連到FortiGate的管理網頁,登入並點選到 "系統" > FortiView > "全部連線對話"
Ensure that the Dst Interface column is visible in the traffic log. If it is not shown, right-click on the title row and select Dst Interface from the dropdown menu. Scroll to the bottom of the menu and select Apply.
確保 Dst Interface(目的介面)的攔位在記錄(Log)中可以被找到。若找不到,在標題列上點右鍵(或在右上角的齒輪上點左鍵),選擇Dst Interface(目的介面),點擊Apply(採用)。
The log shows traffic flowing through both WAN1 and WAN2.
在紀錄中,Dst Interface(目的介面)應該同時檢視到WAN 1及WAN 2的存在,並能檢視到流經兩者的流量。
Disconnect the WAN1 port, continue to browse the Internet, and refresh the traffic log. All traffic is now flowing through WAN2, until you reconnect WAN1.
中斷WAN 1線路的連線(拔線or關閉Wan 1介面),重整網頁後,繼續檢視網頁上的紀錄,更新流量狀態後(左上角有個重整按紐),再次檢視流量紀錄,此時,所有的紀錄中,所有的流量應應全部流經WAN 2線路,直到您恢復WAN 1線路的連線後,才會恢復到WAN1、WAN2並存的狀態。
在紀錄中,Dst Interface(目的介面)應該同時檢視到WAN 1及WAN 2的存在,並能檢視到流經兩者的流量。
Disconnect the WAN1 port, continue to browse the Internet, and refresh the traffic log. All traffic is now flowing through WAN2, until you reconnect WAN1.
中斷WAN 1線路的連線(拔線or關閉Wan 1介面),重整網頁後,繼續檢視網頁上的紀錄,更新流量狀態後(左上角有個重整按紐),再次檢視流量紀錄,此時,所有的紀錄中,所有的流量應應全部流經WAN 2線路,直到您恢復WAN 1線路的連線後,才會恢復到WAN1、WAN2並存的狀態。
(由於尚未進行LAB,故部分翻譯會有差異)
2018年3月26日 星期一
Quick installation using DHCP(使用DHCP功能進行快速安裝)
In this example, you will use DHCP and your FortiGate’s default configuration to securely connect your internal network to the Internet in two simple steps.
在此範例中,您只需要做兩個簡單的步驟,就能使用DHCP功能以及FortiGate的初始設定來安全地連接您的內部網路(Internal network)以及網際網路(Internet)。
(簡單來說,就是利用DHCP功能讓FortiGate設備能夠快速啟用,提供基本防護。)
(需要預先跟ISP業者講好使用DHCP功能,讓FortiGate連接到小烏龜時,可以自動向ISP取得IP,同時,由於FortiGate在internal部分的初始設定就有啟用DHCP功能,底下的電腦只要接上就能自動取得DHCP派發的IP,所以才能做到快速連接,立即使用。)
This recipe has the following requirements:
這個方法有以下幾點需求:
- An ISP that provides connectivity with DHCP and accepts DHCP requests without authentication.
可提供DHCP連線功能並能接受無驗證DHCP請求的ISP業者(通常為中華電信) - A FortiGate with a default configuration that includes a DHCP server on the lan (or internal) interface and a security policy that securely allows all sessions from the Internal network to reach the Internet.
一台具有基本設定的FortiGate,基本設定包含以下兩點:
1:在lan介面存在DHCP server
2:防火牆規則允許內部網路(Internal)接觸到網際網路(Internet) - Your network uses IPv4 to connect to the FortiGate and Internet.
您的網路使用IPv4網路來連接FortiGate及網際網路(Internet)
1. Connecting the FortiGate to your ISP and the internal network
將FortiGate連接到ISP及網際網路上
Connect the FortiGate wan interface to your ISP-supplied equipment.
將FortiGate的Wan端連接到您的ISP業者提供的設備(通常為中華電信的小烏龜)
Connect the internal network to the FortiGate’s default lan or internal interface.
將內部網路(Internal network)連接到FortiGate的預設 lan介面(或是叫Internal介面)
Turn on the ISP’s equipment, the FortiGate unit, and the PCs on the internal network.
啟動ISP業者提供的設備(小烏龜),啟動FortiGate設備,啟動電腦。
2. Configuring your PCs to use DHCP
設定您的電腦使用DHCP功能
For Windows Vista / 7 / 8:
Go to Network and Sharing Center and select Local Area Connections. Select Properties.
開啟"網路及共用中心",開啟"區域連線",開啟"內容"(網路及公用中心可以在"控制台" > "網路和網際網路"找到)
Select Internet Protocol Version 4 (TCP/IPv4), then select Properties.
開啟"網路及共用中心",開啟"區域連線",開啟"內容"(網路及公用中心可以在"控制台" > "網路和網際網路"找到)
Select Internet Protocol Version 4 (TCP/IPv4), then select Properties.
點選到"網際網路通訊協定第4版 (TCP/IPv4)",開啟"內容"
Select Obtain an IP address automatically and Obtain DNS server address automatically.
上半部點選到"自動取得IP位址",下半部點選到"自動取得DNS伺服器位址"
for Mac OS X
Go to Network Preferences and select Ethernet.
開啟網路設定,點選到Ethernet
Set Configure IPv4 to Using DHCP.在設定IPv4的部分選取到使用DHCP
開啟網路設定,點選到Ethernet
Set Configure IPv4 to Using DHCP.在設定IPv4的部分選取到使用DHCP
---------------------------以上為實作-----------以下為驗證----------------------------------
3. Results
From any PC on the internal network, open a web browser and browse to any website. You can successfully connect to the Internet.
從任意一台位在內網的電腦,開啟網頁瀏覽器隨便連個網站,您應該可以成功連上網際網路。
Go to Policy & Objects > IPv4 > Policy. Your Internet-access policy is at the top of list, in the lan – wan section (this section’s name varies based on the FortiGate model).
開啟"政策&物件" > "IPv4" > 政策。
您的防火牆規則位於表單的最上方,位於lan-wan的區域(此區域的名稱會因不同的版本或模式而出現不同的表示名稱,此處截圖的名稱為internal - wan 1)
您的防火牆規則位於表單的最上方,位於lan-wan的區域(此區域的名稱會因不同的版本或模式而出現不同的表示名稱,此處截圖的名稱為internal - wan 1)
View the Count column, which displays the total amount of traffic that has used this policy since the FortiGate’s last reboot. The column should display results, showing that the policy is being used for traffic.
若看不到此攔位count(記數),在標題列上點右鍵(或在右上角的齒輪上點左鍵),選擇Count(記數),點擊Apply(採用)。
2018年1月12日 星期五
Installing a FortiGate in Transparent mode(以透通模式安裝FortiGate)
In this example, you will learn how to connect and configure a new FortiGate unit in Transparent mode to securely connect a private network to the Internet. In Transparent mode, the FortiGate applies security scanning to traffic without applying routing or network address translation (NAT).
在此範例,您將了解如何在透通模式下連接及設定新的FortiGate設備,從而將私有網路安全地連接到網際網路,在透通模式下,FortiGate會對流量進行安全掃描,而不進行路由或轉址的行為。
Warning: Changing to Transparent mode removes most configuration changes made in NAT/Route mode. To keep your current NAT/Route mode configuration, backup the configuration using the System Information widget, found at System > Dashboard > Status.
警告:更改模式為透通模式需要刪除NAT/路由模式中使用的大部分配置,為了保留原NAT/Route模式的設定資料,請照以下步驟操作:左側項目點擊到系統管理(System) > 儀表板(Dashboard) > 狀態(status) > 系統資訊(System Information) > 系統設定(System Configuration) > 設定備份(Backup) > 備份(Backup)
1. Changing the FortiGate’s operation mode
Go to System > Dashboard > Status and locate the System Information widget.
Beside Operation Mode, select Change.
Beside Operation Mode, select Change.
點擊到系統管理(System) > 儀表板(Dashboard) > 狀態(status) > 系統資訊(System Information) > 操作模式(Operation Mode) > 更改(change)
Set the Operation Mode to Transparent. Set the Management IP/Netmask and Default Gateway to connect the FortiGate unit to the internal network.
點選到 透通模式(Transparent),設定管理IP/遮罩(Management IP/Netmaskand)以及用以連接FortiGate設備及內部網路的預設路由(Default Gateway)
點選到 透通模式(Transparent),設定管理IP/遮罩(Management IP/Netmaskand)以及用以連接FortiGate設備及內部網路的預設路由(Default Gateway)
You can now access the GUIby browsing to the Management IP address (in the example, you would browse to http://172.20.120.122).
您現在可以透過瀏覽到先前設定的IP位址登入到圖形化使用者介面進行操作。(在FortiCook網站的範例中,您可瀏覽到網址http://172.20.120.122)
2. (Optional) Setting the FortiGate’s DNS servers
The FortiGate unit’s DNS Settings are set to use FortiGuard DNS servers by default, which is sufficient for most networks. However, if you need to change the DNS servers, go to System > Network > DNS and add Primary and Secondary DNS servers.
FortiGate設備的DNS設定預設是使用FortiGuard的DNS伺服器,這對於大多數的網路環境來說已經足夠使用,但是,若你需要變更DNS伺服器,請照以下步驟操作:點擊到 系統(System) > 網路(Network) > DNS > 指定(Specify) 並設定主要(Primary)及次要(Secondary) 的DNS
3. Creating a policy to allow traffic from the internal network to the Internet
建立一組Policy來允許內部網路到網際網路的流量通過
Go to Policy & Objects > Policy > IPv4 and create a new policy (if your network uses IPv6 addresses, go to Policy & Objects > Policy > IPv6).
點擊到 政策及物件(Policy & Objects) > 政策(Policy) > IPv4 > Create New
(若您的網路使用的是IPv6位址,點擊到 政策及物件(Policy & Objects) > 政策(Policy) > IPv6,ps:若沒看到IPv6,則需要先到進階項目中開啟IPv6)
(若您的網路使用的是IPv6位址,點擊到 政策及物件(Policy & Objects) > 政策(Policy) > IPv6,ps:若沒看到IPv6,則需要先到進階項目中開啟IPv6)
Set the Incoming Interface to an available external interface (typically port 1) and the Outgoing Interfaceto the Internet-facing interface (typically WAN1)
將來源介面設為可用的外部介面(通常為Port 1),並將出去介面設為網際網路方面的介面(通常為WAN 1)
Scroll down to view the Logging Options. In order to view the results later, enable Log Allowed Traffic and select All Sessions.
將畫面向下捲動,檢視到紀錄項目(Logging Options),為了稍後能夠檢視到結果,啟用 允許紀錄流量(Log Allowed Traffic),並選取到 所有流量(All Sessions)
4. Connecting the network devices
連接到網路設備
Go to System > Dashboard > Status and locate the System Resources widget. Select Shutdown to power off the FortiGate unit.
點擊到 系統(System) > 儀錶板(Dashboard) > 狀態(Status) 並檢視到 系統資源(System Resources) 分頁,點擊到 關機(Shutdown)以關閉FortiGate設備
Alternatively, you can enter the following command in the CLI Console (also found by going to
System > Dashboard > Status): execute shutdown
另外,您也可以在命令列介面輸入以下指令達到相同目的:execute shutdown
(點擊到系統(System) > 儀錶板(Dashboard) > 狀態(Status) 並檢視到CLI Console,在畫面中以滑鼠點擊左鍵即可進入介面)
System > Dashboard > Status): execute shutdown
另外,您也可以在命令列介面輸入以下指令達到相同目的:execute shutdown
(點擊到系統(System) > 儀錶板(Dashboard) > 狀態(Status) 並檢視到CLI Console,在畫面中以滑鼠點擊左鍵即可進入介面)
Wait until all the lights, except for the power light, on your FortiGate have turned off. If your FortiGate has a power button, use it to turn the unit off. Otherwise, unplug the unit.
You can now connect the FortiGate unit between the internal network and the router
(在實體環境下仍須注意斷線問題,最好確認不會影響到內部網路的時間再進行安裝。)
Connect the wan1 interface to the router internal interface and connect the internal network to the FortiGate internal interface port.
連接Wan1介面到Router的對內介面並連接內部網路到FortiGate的internal介面Port
Power on the FortiGate unit. 接好就啟動電源
5. Results
結果
You can now browse the Internet using any computer that connects to the FortiGate’s internal interface.
You can view information about the traffic being processed by your FortiGate by going to System > FortiView > All Sessions and finding traffic that has port 1 as the Src Interface and the Internet-facing interface as the Dst Interface.
點擊到 System > FortiView > All Sessions,要找到您瀏覽網頁的紀錄,請分別確認來源(Src Interface)為內網(internal)以及目的(Dst Interface)為連接網際網路的介面(通常為Wan1)
If these two columns are not shown, select Column Settings and move Src Interface and Dst Interface to the list of fields to be shown.
(系統版本不同,則部分介面也會有不同的外觀或位在不同的地方)
訂閱:
意見 (Atom)






















