In this example, you will learn how to connect and configure a new FortiGate unit in Transparent mode to securely connect a private network to the Internet. In Transparent mode, the FortiGate applies security scanning to traffic without applying routing or network address translation (NAT).
在此範例,您將了解如何在透通模式下連接及設定新的FortiGate設備,從而將私有網路安全地連接到網際網路,在透通模式下,FortiGate會對流量進行安全掃描,而不進行路由或轉址的行為。
Warning: Changing to Transparent mode removes most configuration changes made in NAT/Route mode. To keep your current NAT/Route mode configuration, backup the configuration using the System Information widget, found at System > Dashboard > Status.
警告:更改模式為透通模式需要刪除NAT/路由模式中使用的大部分配置,為了保留原NAT/Route模式的設定資料,請照以下步驟操作:左側項目點擊到系統管理(System) > 儀表板(Dashboard) > 狀態(status) > 系統資訊(System Information) > 系統設定(System Configuration) > 設定備份(Backup) > 備份(Backup)
1. Changing the FortiGate’s operation mode
Go to System > Dashboard > Status and locate the System Information widget.
Beside Operation Mode, select Change.
Beside Operation Mode, select Change.
點擊到系統管理(System) > 儀表板(Dashboard) > 狀態(status) > 系統資訊(System Information) > 操作模式(Operation Mode) > 更改(change)
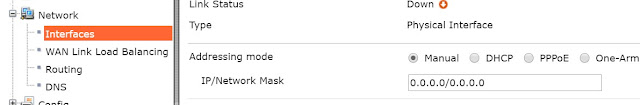
Set the Operation Mode to Transparent. Set the Management IP/Netmask and Default Gateway to connect the FortiGate unit to the internal network.
點選到 透通模式(Transparent),設定管理IP/遮罩(Management IP/Netmaskand)以及用以連接FortiGate設備及內部網路的預設路由(Default Gateway)
點選到 透通模式(Transparent),設定管理IP/遮罩(Management IP/Netmaskand)以及用以連接FortiGate設備及內部網路的預設路由(Default Gateway)
You can now access the GUIby browsing to the Management IP address (in the example, you would browse to http://172.20.120.122).
您現在可以透過瀏覽到先前設定的IP位址登入到圖形化使用者介面進行操作。(在FortiCook網站的範例中,您可瀏覽到網址http://172.20.120.122)
2. (Optional) Setting the FortiGate’s DNS servers
The FortiGate unit’s DNS Settings are set to use FortiGuard DNS servers by default, which is sufficient for most networks. However, if you need to change the DNS servers, go to System > Network > DNS and add Primary and Secondary DNS servers.
FortiGate設備的DNS設定預設是使用FortiGuard的DNS伺服器,這對於大多數的網路環境來說已經足夠使用,但是,若你需要變更DNS伺服器,請照以下步驟操作:點擊到 系統(System) > 網路(Network) > DNS > 指定(Specify) 並設定主要(Primary)及次要(Secondary) 的DNS
3. Creating a policy to allow traffic from the internal network to the Internet
建立一組Policy來允許內部網路到網際網路的流量通過
Go to Policy & Objects > Policy > IPv4 and create a new policy (if your network uses IPv6 addresses, go to Policy & Objects > Policy > IPv6).
點擊到 政策及物件(Policy & Objects) > 政策(Policy) > IPv4 > Create New
(若您的網路使用的是IPv6位址,點擊到 政策及物件(Policy & Objects) > 政策(Policy) > IPv6,ps:若沒看到IPv6,則需要先到進階項目中開啟IPv6)
(若您的網路使用的是IPv6位址,點擊到 政策及物件(Policy & Objects) > 政策(Policy) > IPv6,ps:若沒看到IPv6,則需要先到進階項目中開啟IPv6)
Set the Incoming Interface to an available external interface (typically port 1) and the Outgoing Interfaceto the Internet-facing interface (typically WAN1)
將來源介面設為可用的外部介面(通常為Port 1),並將出去介面設為網際網路方面的介面(通常為WAN 1)
Scroll down to view the Logging Options. In order to view the results later, enable Log Allowed Traffic and select All Sessions.
將畫面向下捲動,檢視到紀錄項目(Logging Options),為了稍後能夠檢視到結果,啟用 允許紀錄流量(Log Allowed Traffic),並選取到 所有流量(All Sessions)
4. Connecting the network devices
連接到網路設備
Go to System > Dashboard > Status and locate the System Resources widget. Select Shutdown to power off the FortiGate unit.
點擊到 系統(System) > 儀錶板(Dashboard) > 狀態(Status) 並檢視到 系統資源(System Resources) 分頁,點擊到 關機(Shutdown)以關閉FortiGate設備
Alternatively, you can enter the following command in the CLI Console (also found by going to
System > Dashboard > Status): execute shutdown
另外,您也可以在命令列介面輸入以下指令達到相同目的:execute shutdown
(點擊到系統(System) > 儀錶板(Dashboard) > 狀態(Status) 並檢視到CLI Console,在畫面中以滑鼠點擊左鍵即可進入介面)
System > Dashboard > Status): execute shutdown
另外,您也可以在命令列介面輸入以下指令達到相同目的:execute shutdown
(點擊到系統(System) > 儀錶板(Dashboard) > 狀態(Status) 並檢視到CLI Console,在畫面中以滑鼠點擊左鍵即可進入介面)
Wait until all the lights, except for the power light, on your FortiGate have turned off. If your FortiGate has a power button, use it to turn the unit off. Otherwise, unplug the unit.
You can now connect the FortiGate unit between the internal network and the router
(在實體環境下仍須注意斷線問題,最好確認不會影響到內部網路的時間再進行安裝。)
Connect the wan1 interface to the router internal interface and connect the internal network to the FortiGate internal interface port.
連接Wan1介面到Router的對內介面並連接內部網路到FortiGate的internal介面Port
Power on the FortiGate unit. 接好就啟動電源
5. Results
結果
You can now browse the Internet using any computer that connects to the FortiGate’s internal interface.
You can view information about the traffic being processed by your FortiGate by going to System > FortiView > All Sessions and finding traffic that has port 1 as the Src Interface and the Internet-facing interface as the Dst Interface.
點擊到 System > FortiView > All Sessions,要找到您瀏覽網頁的紀錄,請分別確認來源(Src Interface)為內網(internal)以及目的(Dst Interface)為連接網際網路的介面(通常為Wan1)
If these two columns are not shown, select Column Settings and move Src Interface and Dst Interface to the list of fields to be shown.
(系統版本不同,則部分介面也會有不同的外觀或位在不同的地方)